When it comes to ensuring safety and responsibility on the Internet, proper education and a policy of mutual trust and respect are the best policies. But who am I kidding? The web is a vast playground of debauchery and anthropological horrors, and it’s a teenager’s prerogative to peer occasionally over the Gates of Mordor into the land of shadows. From porn and bomb-building guides to Facebook and Twitter, the Internet is a vast cornucopia of potentially hazardous material. For the most part, I’m of the opinion that a little bit of minor mischief is harmless, and perhaps even character building, as long as they come out relatively unscathed. But if you’re interested in sheltering your child, there’s an equally lavish smorgasbord of parental control and net nannying tools at your disposal.
The logical route for today’s concerned, yet lazy, parent, is to shell out hundreds of bucks for some off-the-shelf piece of software that they can install on their kid’s computer. The problem is that a quick Google search reveals a dozen workarounds for even the most expensive parental censoring spy tools. Making matters worse, by installing the software on their machine, you’re immediately tipping your hand by revealing that [A] you are watching them and [B] which tool you are using.
The better way to do things is to take a page out of the government’s book and surreptitiously and warrantlessly monitor all Internet traffic that goes out of your house. This process is better because it prevents them from using a browser with an Incognito Mode or just clearing the browser history (perhaps the first thing a mischievous tot learns how to do on the computer). If only there were some gateway that stood between your house and the World Wide Web…oh wait, there is. It’s your router.
In this tutorial, I’ll show you how to retrieve the web traffic log from a NETGEAR WPN824v2 router and how to block individual websites for selected computers in your house—all without installing a single piece of software on your kid’s computer.
[Note: If you have a NETGEAR router, the steps will probably be similar, but may vary slightly. If you have another router, such as a Linksys, Belkin, ASUS, or D-Link router, the steps will look entirely different. But I’m willing to bet you can achieve the same outcome by poking around.]
Accessing Your Router’s Settings Page
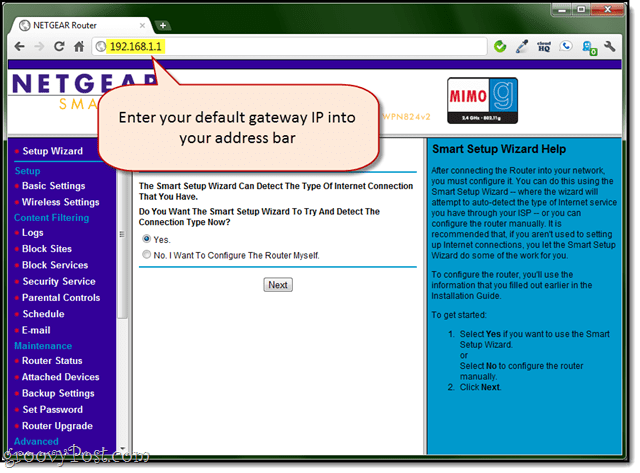
From any computer, access your router’s setup page by typing in its IP address into your browser window. For me, it’s 192.168.1.1. Try clicking that and see what happens.
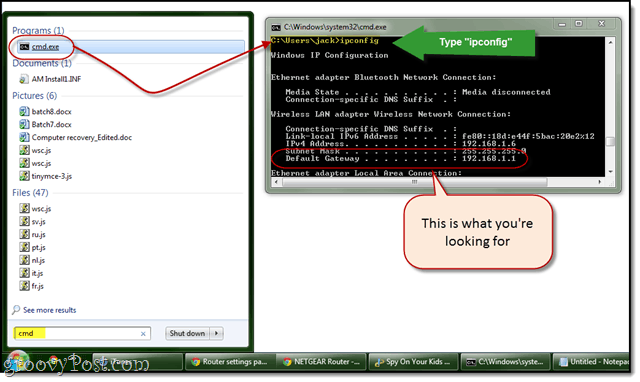
If that doesn’t work, open CMD.exe and type ipconfig /all and look for the field that reads default gateway.
A Quick Note About Your Default Password
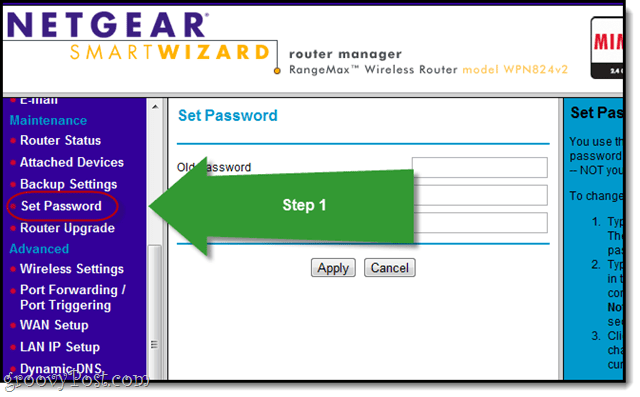
You’ll probably be prompted to enter a username and password. You probably don’t remember what this is. Try admin / password or admin / 1234 or admin / admin or root / root. You can also Google your router’s model number and “default password.” Once you’ve done that, you should change it. On the NETGEAR page, it’s Maintenance > Set Password
Viewing Your Logs
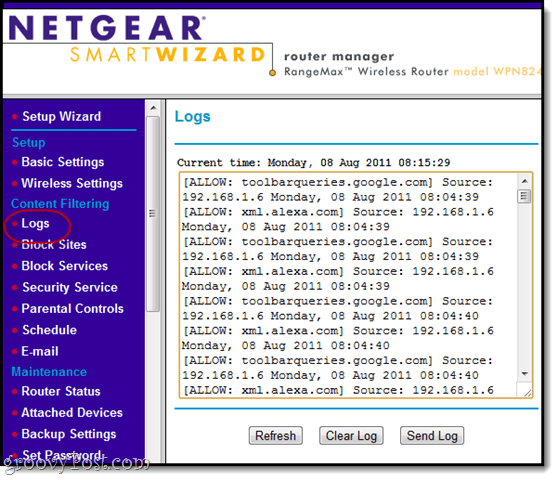
To get a feel for what we’re working with, go ahead and Click Logs under “Content Filtering.”
Initially, this is going to be a bunch of mumbo jumbo. But don’t worry, we’ll make sense of this. If you can already parse out all this info, then great. If not, read on.
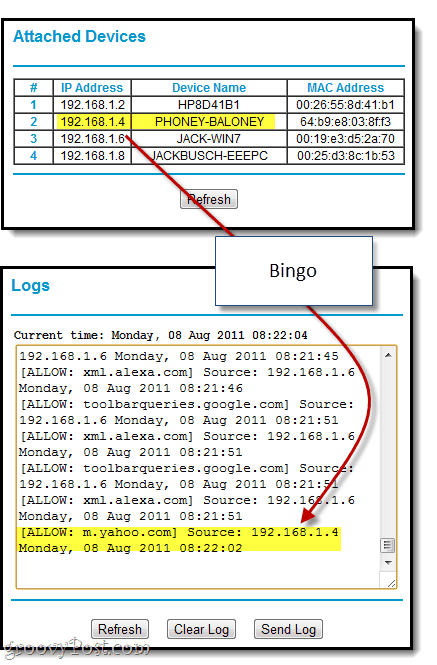
What you want to pay attention to in this screenshot are the IP addresses for the Source. Using this information, we’ll track who was looking at what. Here, we see that all the activity is coming from 192.168.1.6. That’s my computer. How do we know? See below.
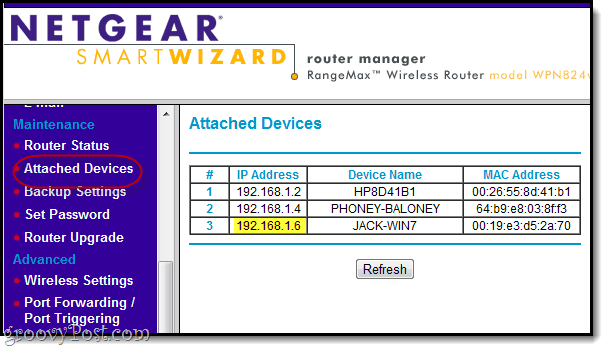
Viewing Attached Devices
Click Attached Devices under “Maintenance” to see.
This lists all the devices that are connecting to the router. As you can see, 192.168.1.6 is JACK-WIN7, which is what I named my main computer. PHONEY-BALONEY is my iPhone. HP8D41B1, I’m assuming, is the netbook sitting open on my kitchen table. Or it could be my neighbor stealing my WiFi. At any rate, this is a useful page to remember.
To illustrate, I’ll visit yahoo.com on my iPhone and see if it shows up in the logs:
Now, I’m going to hazard a guess and assume that you don’t want to spend your evenings sifting through the log, matching up IP addresses to salacious websites. Luckily, you can automate it somewhat by blocking sites.
Blocking Sites
Blocking sites and services on your router restrict access to certain websites or activity on certain ports. This is a rock solid way to police web activity because it can’t be circumvented from a computer. You have to access the router to change this.
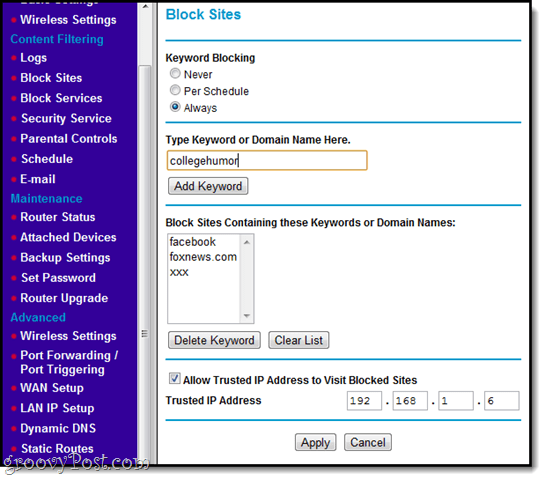
Click Block Sites under “Content Filtering.” Here, you can enforce restricted websites by entering keywords you want to be blocked. You can choose to block sites according to a schedule (ClickSchedule to choose the times/days of the week to block) or you can elect to block them always.
Notice along the bottom that you can add a trusted IP address. In this case, I don’t want to block myself from these sites, just my untrustworthy kids. Remember that my IP address is 192.168.1.6, so we can punch it in here to give us full access. Note that this presents a potential workaround, as a clever user could find a way to get assigned that IP. Use at your own peril.
Now, when you try to visit a blocked site, you see this:
Note that one may be able to circumvent this kind of filtering by typing in an IP address directly (for example, to get to Facebook, just type 69.63.189.11 into the browser window). To avoid this, add the known IP addresses to your block list.
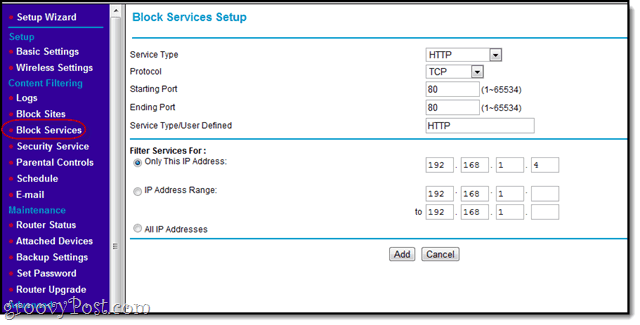
Tip: If you want to block all Internet access, say, after 9 PM, use the Block Services tab and choose HTTP from the drop down. Then make sure you specify the IP address for the restricted devices.
E-mail and Alerts
Using the E-mail tab, you can have your router email you the logs on a daily/weekly/hourly basis or each time someone tries to access a blocked website. Or, you can send the logs manually from the Logs page.
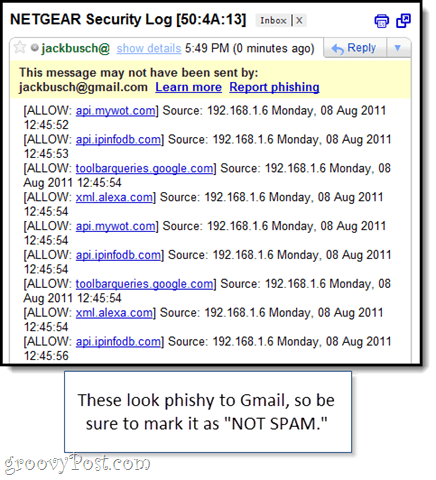
Either way, the email will usually show up in your Spam folder, so be sure you filter it correctly.
What I suggest doing, rather than actively blocking sites, is to set yourself up a Gmail filter that scans your logs for certain keywords and then stars them. This will save you a lot of time sifting through the logs manually and also prevents your suspects from knowing that you’re monitoring their activity.
With a filter like this, you can get a daily report of your son or daughter’s web activity, as well as a flag each time certain keywords show up. All without them knowing.
Conclusion
Using NETGEAR’s built-in security tools, you can easily monitor all network traffic going into or coming out of your home. The advantage of this is that there isn’t any software installed on your child’s computer, meaning that it’s harder for them to detect and nearly impossible for them to get around. They could use proxy sites, but that’s a pain in the butt and easily picked up on if you look at the logs. The main limitation is that you won’t be able to see any web browsing that’s done on their smartphone or tablet via a cellular data network (e.g. 4G, LTE).
And I want to reiterate that properly educating your kid about safe web browsing activities is the first and most important step to keeping them in the clear on the web. A lot worse can happen to anyone on the web who doesn’t know basic web safety principles. And that goes beyond watching bootlegged episodes of South Park or a risqué CollegeHumor.com video. From viruses and phishing schemes to sexual predators and dangerous misinformation from irresponsible news journalists, there’s a lot out there that can harm your child and your family that can’t be stopped through Big Brother-style monitoring. Your energy is far better spent trying to teach your kid to be a responsible and thoughtful consumer of media.
But if you are ever suspicious that your kid is involved in something way over his or her head, these tools may be able to help you catch it before something disastrous happens.
Okay, enough preaching. Godspeed, you paranoid parent, and happy spying.
via groovypost